When I tell people I work in cybersecurity, I usually get one of two reactions: either their eyes light up because they think it sounds cool, or they immediately say, "Oh, I could never do that! I'm not technical enough." I get it. Cybersecurity sounds intimidating. It feels like a field reserved for people who've been coding since they were ten or who can rattle off networking protocols in their sleep.But here's a secret: cybersecurity isn't one thing. It's not just hacking or writing code. It's a collection of different fields, each requiring different strengths. Some roles focus on investigation and research. Others involve writing policies and making sure organizations follow the rules. Yes, some jobs require deep technical knowledge, but many don't. You don't need to be a networking expert to analyze threat intelligence or audit compliance controls.If you're considering a career change into cybersecurity, you're probably wondering where you'd even fit. In this post, we'll break down what cybersecurity actually is and explore the different fields within it. By the end, you'll see that there's likely a path that matches your interests and strengths, even if you've never worked in tech before.
So, What Is Cybersecurity?
Cybersecurity is the practice of protecting computers, networks, and data from people who want to steal, damage, or misuse them. Think of it like digital defense work. Just as a city needs police officers, firefighters, and emergency planners to stay safe, the digital world needs people who can stop attacks, respond to problems, and build better defenses.
But here's what many people don't realize: cybersecurity isn't just one job or one set of skills. It's actually many different fields working together. Some people write code to find weak spots in software. Others watch networks for suspicious activity. Some focus on creating rules and checking that companies follow them. Others investigate what happened after an attack.
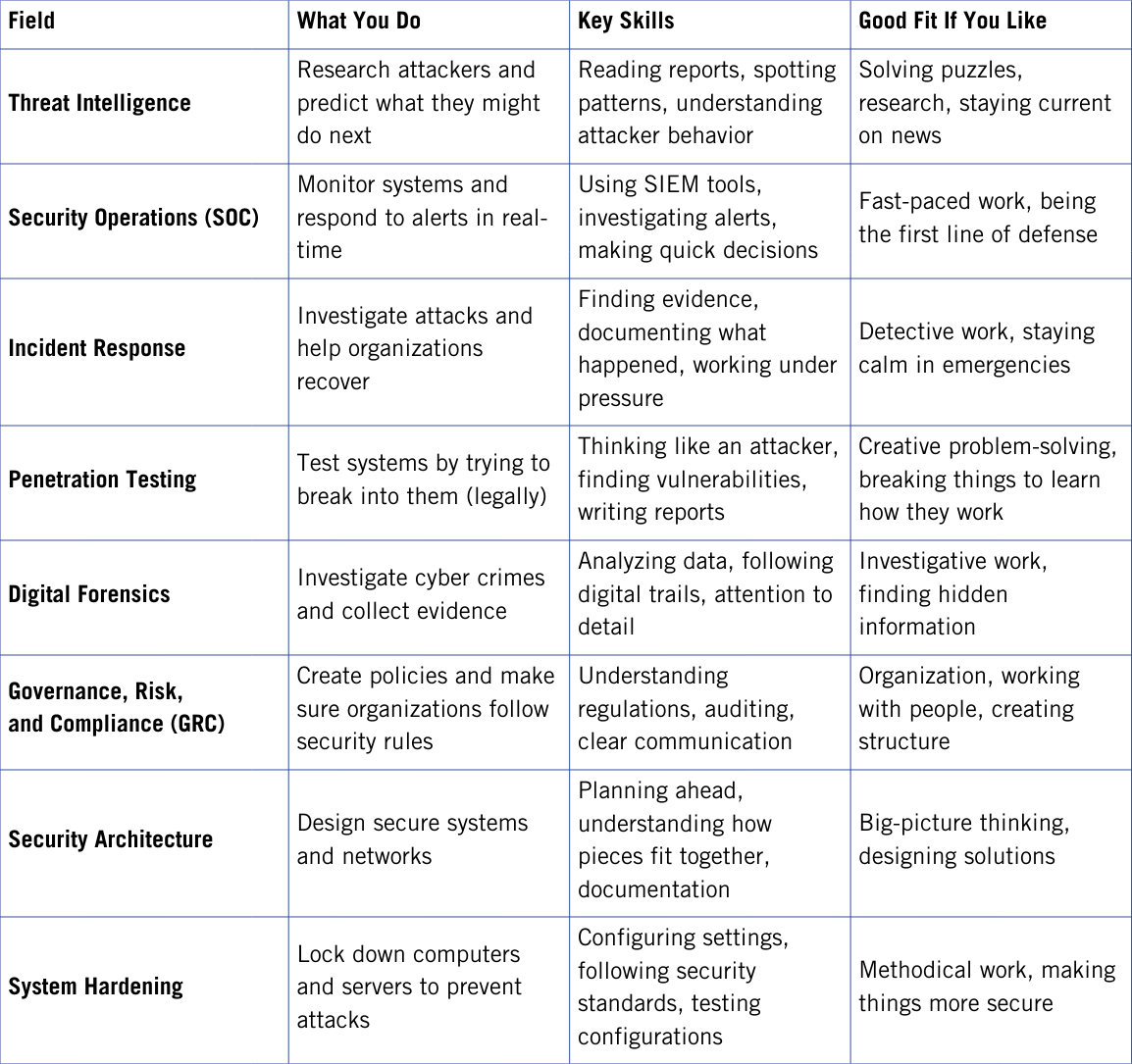
You don't need to be an expert in everything to work in cybersecurity. If you like solving puzzles and understanding how attackers think, threat intelligence might fit you. If you enjoy investigating and finding evidence, digital forensics could be your path. If you're interested in rules, compliance, and making sure organizations follow best practices, governance and risk work doesn't require deep networking knowledge.
Cybersecurity Fields at a Glance
Where Do Cybersecurity Professionals Work?
Cybersecurity shows up in almost every industry, and the type of work you do can look pretty different depending on where you land. Here are a few examples of how cybersecurity plays out in different settings.
Government: Federal and state agencies protect sensitive citizen information and critical infrastructure. The U.S. Department of Homeland Security, for instance, monitors federal networks for potential cyberattacks that could affect national security. If you work in government cybersecurity, you might focus on threat detection or ensuring systems meet strict compliance standards.
Finance: Banks and financial institutions are constant targets for fraud and theft. Cybersecurity professionals in finance build systems that watch for unusual transaction patterns and protect customer accounts. They also make sure the organization meets regulations like PCI-DSS, which sets security standards for handling credit card information.
Healthcare: Hospitals and clinics store massive amounts of private medical data, making them attractive targets for ransomware attacks. Cybersecurity teams in healthcare investigate suspicious emails, protect patient records, and respond quickly when attacks happen. The stakes are high because a security breach can directly impact patient care.
Retail: Big retailers like Walmart and Target handle millions of customer transactions and store payment information. Cybersecurity teams test online shopping platforms for vulnerabilities, monitor for breaches, and work to prevent credit card theft. During busy shopping seasons, the pressure to keep systems secure and running smoothly increases.
No matter the industry, the goal stays the same: protect data and systems from people trying to exploit them.
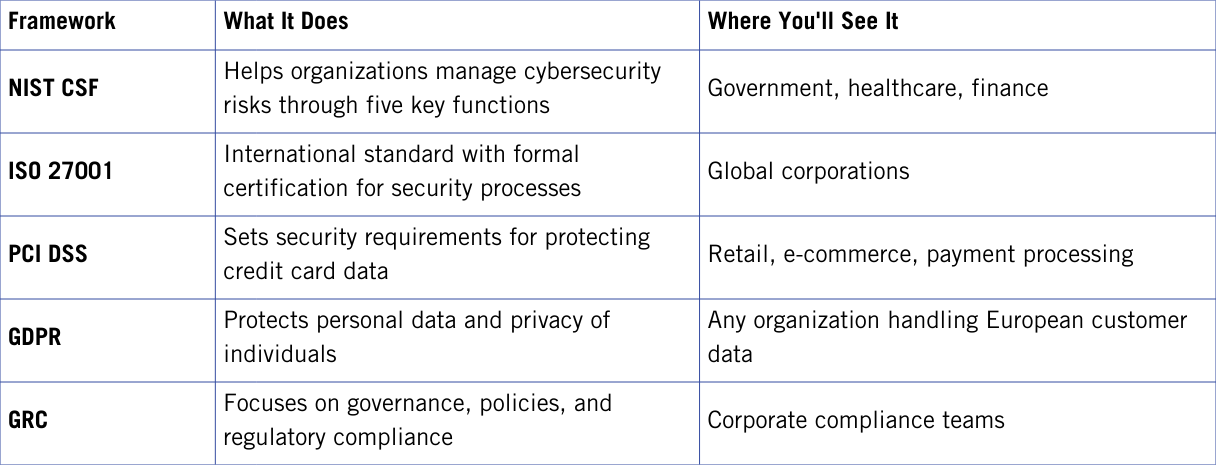
Understanding Cybersecurity Frameworks
If you start exploring cybersecurity jobs, you'll probably see employers mention frameworks like NIST or ISO 27001. So what are these, and why do they matter?
A cybersecurity framework is basically a set of guidelines that helps organizations build and manage their security programs. Instead of every company inventing its own approach from scratch, they can follow a proven structure that covers the important bases.
NIST Cybersecurity Framework (CSF) is one of the most common frameworks you'll encounter, especially in government and corporate jobs. Created by the National Institute of Standards and Technology, it organizes cybersecurity work into five core functions:
- Identify: Understand what assets and data need protection
- Protect: Put safeguards in place to limit damage
- Detect: Monitor systems to catch problems early
- Respond: Take action when something goes wrong
- Recover: Get back to normal operations after an incident
ISO 27001 is an international standard focused on information security management. Organizations can get formally certified in ISO 27001, which shows they follow rigorous security practices. You'll see this framework more often in global companies.
PCI DSS (Payment Card Industry Data Security Standard) is required for any organization that handles credit card information. If you work in retail, e-commerce, or finance, you'll likely encounter PCI DSS. It sets specific technical requirements for protecting payment data.
GDPR (General Data Protection Regulation) is a European regulation that protects personal data and privacy. Even if you work for a U.S. company, if that company handles data from European customers, GDPR applies. Many organizations now follow GDPR principles regardless of location because it represents strong data protection practices.
GRC (Governance, Risk, and Compliance) isn't a single framework but rather an approach that focuses on policies, controls, and making sure organizations follow regulations. If you're interested in the policy and audit side of cybersecurity, GRC work might appeal to you.
Quick Framework Comparison
Many employers look for candidates who understand these frameworks because they provide a common language for talking about security. You don't need to memorize every detail before starting, but knowing they exist and what they cover will help as you learn.
What Should You Know Before Starting?
You don't need an advanced technical background to start learning cybersecurity, but having a baseline in a few key areas will make your learning path smoother. Think of these as helpful foundations, not strict requirements.
If you're completely new to tech, don't panic. Many successful cybersecurity professionals started exactly where you are. The key is building comfort with some basic concepts before diving into specialized security topics like encryption or threat detection.
Here are areas worth getting familiar with before you start:
Computer basics: You should feel comfortable managing files, installing software, and using tools like spreadsheets. If you can navigate your computer confidently and troubleshoot minor issues, you're in good shape.
How networks work: Understanding the basics of how the internet functions, what IP addresses are, and how routers connect devices will help you grasp security concepts later. You don't need to be a networking expert, just familiar with the fundamentals.
Operating systems: Cybersecurity work often involves both Windows and Linux environments. Getting comfortable navigating both, even at a basic level, will serve you well. Linux especially shows up frequently in security tools and labs.
Basic math: You don't need advanced calculus, but comfort with algebra and simple probability helps when you get into topics like encryption and risk assessment. If math makes you nervous, focus on understanding logic and patterns instead.
Programming logic: You don't need to be a developer, but understanding how variables, loops, and conditional statements work will help when you learn scripting languages like Python. Many cybersecurity tasks involve automating repetitive work through scripts.
These skills prepare you to work with real security tools, from analyzing network traffic in Wireshark to managing cloud security in AWS. If you're missing some of these foundations, that's okay. You can learn them as you go or refresh them before starting a structured program. The most important thing is being willing to learn and staying curious.
Conclusion
Cybersecurity is a big field with room for all kinds of people. You don't need to master everything to find your place. Whether you're drawn to solving puzzles, investigating incidents, designing secure systems, or making sure organizations follow the rules, there's a role that fits.
The most important thing? Start exploring. Try different areas, see what clicks, and remember that everyone in this field started somewhere, often without knowing much about cybersecurity at all.
Ready to explore further? Check out these free resources:
- CyberSeek – See cybersecurity job openings in your state and explore career pathways
- NICE Framework Cyber Career Pathways Tool – An interactive tool that shows different cybersecurity work roles and the skills they require
- CAE Cybersecurity Career Explorer – Browse federal cybersecurity job postings
FAQs
Why is cybersecurity important?
Cybersecurity is important because it protects the systems and data that people and organizations rely on every day. Without it, sensitive information like medical records, financial data, and personal communications would be vulnerable to theft or damage. Cybersecurity keeps businesses running, protects people's privacy, and helps prevent attacks that could disrupt critical services like hospitals, banks, and government agencies.
What does a cybersecurity analyst do?
A cybersecurity analyst monitors systems for threats, investigates alerts, and responds to security incidents. They use tools to detect suspicious activity, analyze what happened during an attack, and help prevent future issues. Cybersecurity analysts often work in the Security Operations Center (SOC) and are typically one of the first lines of defense against cyber threats.
What is network security vs cybersecurity?
Network security is a part of cybersecurity. Cybersecurity is the broad practice of protecting all digital assets, including computers, data, applications, and networks. Network security specifically focuses on protecting the infrastructure that connects systems, like routers, firewalls, and the traffic moving between devices. Think of cybersecurity as the whole house, and network security as the locks on the doors and windows.
What is information security vs cybersecurity?
Information security and cybersecurity are closely related, but have different focuses. Information security protects data in any form, whether it’s digital, physical (like paper files), or spoken. Cybersecurity specifically protects digital systems, networks, and data from cyber threats. In practice, cybersecurity is often considered a subset of information security, focusing on the digital side of protecting information.
What is the first step in cybersecurity for beginners?
Start by exploring the different fields to see what interests you. Use free resources like the NICE Framework Cyber Career Pathways Tool or CyberSeek to learn about different roles and what they involve. Read about the work, watch videos, and see which areas match your strengths. Once you have a general direction, you can begin learning the basics through online courses, certifications, or bootcamp programs. The key is to start exploring without feeling like you need to commit to one path right away.
What is a cybersecurity framework (NIST, ISO 27001)?
A cybersecurity framework is a set of guidelines that helps organizations manage security risks and protect their systems. NIST (National Institute of Standards and Technology) created the Cybersecurity Framework, which organizes security work into five functions: Identify, Protect, Detect, Respond, and Recover. ISO 27001 is an international standard that focuses on information security management systems. Both frameworks give organizations structured ways to build and maintain security programs, and many employers look for familiarity with these frameworks when hiring.
What is ransomware/phishing in cybersecurity terms?
Ransomware is malicious software that locks or encrypts a victim’s files and demands payment to restore access. It’s one of the most common and damaging cyber threats, often targeting businesses or healthcare organizations. Phishing is a social engineering attack where criminals send fake emails or messages pretending to be trustworthy sources to trick people into sharing passwords, credit card numbers, or other sensitive information. Both are major threats that cybersecurity professionals work to prevent, as well as respond to.
What is cybersecurity?
Cybersecurity is the practice of protecting computers, networks, and data from people who want to steal, damage, or misuse them. It includes many different fields, from monitoring systems for threats to investigating attacks to creating policies that keep organizations secure.
What skills do you need for cybersecurity?
The skills you need depend on which field you choose. Some roles require technical skills like using security tools or understanding networks. Others focus on research, communication, or policy work. Problem-solving, attention to detail, and curiosity are valuable across all cybersecurity fields.
Do you need a degree to work in cybersecurity?
No. Many people enter cybersecurity through bootcamps, certifications, or self-study. Employers often care more about hands-on skills and the ability to solve problems than formal degrees. Career changers from fields like IT support, teaching, or military service are common in cybersecurity.

.png)


.png)